
A trio of e mail authentication requirements work collectively to enhance e mail deliverability for the sender and e mail security for the recipient.
Sender Coverage Framework (SPF), DomainKeys Recognized Mail (DKIM), and Area-based Message Authentication, Reporting, and Conformance (DMARC) assist to make sure that emails despatched out of your firm are actual and that malicious actors usually are not spoofing or in any other case tampering with them.
SPF, DKIM, DMARC
SPF, DKIM, and DMARC present the receiving e mail server {that a} given message was despatched from a certified IP deal with, that the sender is genuine, and that the sender is clear about its id.
Let’s take every one in flip.
Establishing SPF data in your area includes including a kind of TXT file containing a certified listing of outgoing mail servers to the Area Title System (DNS). SPF verifies that emails from your online business’s area come from an authenticated supply, not an imposter.
DKIM keys include two elements: a public key saved within the DNS and a non-public key saved on the sending mail server. The DKIM signature connected to every outgoing e mail is utilized by recipients’ mail servers to confirm its authenticity. DKIM also can point out if a given e mail message has been altered.
DMARC is a coverage mechanism that enables an organization to regulate how incoming emails from its area must be dealt with in the event that they fail the SPF or DKIM authentication. The choices are “reject,” “quarantine,” or “none.” This may be like an alarm bell if a wrong-doer is making an attempt to make use of your area.
SPF Information
Establishing an SPF file requires entry to your area’s DNS data on the registrar, corresponding to GoDaddy or comparable. You probably have ever needed to confirm your area or transfer it to a brand new server you doubtless up to date its DNS file.
An SPF file is just a TXT file in your area’s DNS.
The SPF file will likely be of the sort “TXT.” And it’ll begin with the model of SPF you’re utilizing.
v=spf1
The model is adopted by a listing of licensed IP4 or IP6 addresses, as in:
v=spf1 ip4:192.168.0.1
This SPF file would authorize emails from the 192.168.0.1 IP deal with. To permit a spread of IP addresses, you could possibly use Classless Inter-Area Routing (CIDR) notation (generally known as “slash” notation).
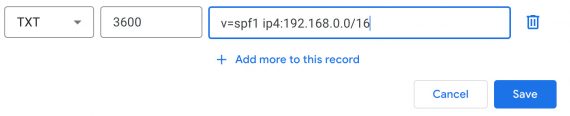
v=spf1 ip4:192.168.0.0/16
The above SPF file would authorize a spread of IP addresses from 192.168.0.0 to 192.168.255.255 — that is what the “/16” signifies.
Utilizing the prefix “a,” an SPF file can authorize a site by identify. The file beneath authorizes a server related to the instance.com area.
v=spf1 a:instance.com
Equally, the prefix “mx” (“mail trade”) authorizes particular mail servers.
v=spf1 mx:mail.instance.com
To authorize a third-party sender, use the prefix “embrace.” The instance beneath permits each an IP vary and Google servers.
v=spf1 ip4:192.168.0.0/16 embrace:_spf.google.com
There are additionally two SPF qualifiers. The primary is ~all with a tilde (~). The second is -all with a hyphen (-).
The tilde model (~all) is a soft-fail qualifier. Usually, the receiving e mail server will settle for messages from senders that aren’t within the related SPF file however contemplate them to be suspicious.
The hyphen model (-all) is a hard-fail qualifier. The receiving e mail server will doubtless label messages despatched from a server not licensed within the SPF file as spam and reject them.
Lastly, all of those could also be used collectively for comparatively advanced authorizations.
v=spf1 ip4:192.168.0.0/16 a:instance.com embrace:_spf.google.com
Bear in mind, SPF data assist the receiving e mail servers establish genuine e mail messages out of your firm’s area.
DKIM Keys
DKIM protects your area and helps to stop anybody from impersonating your organization. The 2 DKiM keys enable the recipient’s e mail server to confirm that your organization despatched the message and that it was not altered after you despatched it.
Step one in organising DKIM is producing the keys — one public and one personal. The personal secret is safe on the server used for sending emails out of your area. The general public secret is added to the DNS as a TXT file.
The difficult half is producing the keys for the reason that precise process for creating them varies from one e mail service supplier to the following. And it’s fully completely different if your organization hosts its personal mail server.
Electronic mail service suppliers supply directions. Listed here are a number of examples in no specific order.
- Mailchimp: Set Up Electronic mail Area Authentication,
- Klaviyo: How you can Arrange a Devoted Sending Area,
- Zoho Campaigns: How you can Authenticate My Area,
- MailerLite: Electronic mail area authentication,
- Campaigner: DKIM, SPF, and DMARC,
- ConvertKit: Utilizing a Verified Area for Electronic mail Sending,
- MailUp: Maximizing Deliverability for Your Emails,
- ActiveCampaign: SPF, DKIM, and DMARC Authentication,
- Keap: DKIM.
In every case, the DKIM is accomplished once you add — copy and paste — the e-mail supplier’s CNAME file to your area’s DNS. This file(s) represents the general public key to authenticate your organization’s outbound e mail advertising and marketing messages.
DMARC
DMARC gives one other layer of safety and in addition instructs e mail servers what to do with messages that fail SPF or DKIM authentication.
The muse of DMARC is a TXT file positioned in your area’s DNS. It will include the DMARC coverage with not less than two components:
- An e mail deal with to obtain combination reviews of e mail authentication, and
- The motion to tackle emails that fail authentication (i.e., reject or quarantine).
Right here’s an instance DMARC TXT file in a DNS:
v=DMARC1; p=quarantine; rua=mailto:armando@instance.com; ruf=mailto:armando@instance.com.
The file begins with the DMARC model.
v=DMARC1;
The “p” factor assigns the motion for emails that fail authentication. On this case, it’s set to “quarantine,” which instructs the receiving server to maneuver such messages to a holding space. Different choices embrace “none” — which doesn’t cease the e-mail however screens SPF or DKIM failures — or “reject.”
p=quarantine;
The prefixes “rua” and “ruf” inform the receiving server the place to ship combination reviews (rua — Reporting URI for Combination knowledge) and forensic reviews (ruf — Reporting URI for Failure knowledge). These reviews can disclose a felony trying to impersonate your online business.
Further modifiers embrace:
- pct — the share of e mail messages subjected to the DMARC coverage.
- sp — the DMARC coverage for subdomains.
- adkim — assigns strict (adkim:s) or relaxed (adkim:r) mode for DKIM.
- aspf — assigns strict (adkim:s) or relaxed (adkim:r) mode for SPF.
Third-party providers will help generate a DMARC file based mostly on the official customary. These providers embrace:
Defend Sender and Recipients
Establishing SPF, DKIM, and DMARC data in your area ensures that e mail servers acknowledge messages out of your firm as genuine and reject imposters. The end result protects your organization’s repute and shields prospects from phishing assaults and different varieties of e mail fraud.